Blog

Tutorial: How to Check Your Network Perimeter Using Port Scanning
By Dave West | Apr 09, 2019 | Insights
Anyone who has ever had to provide access to networked services, secure hosts on a network and/or troubleshoot access to networked services may be very familiar with questions like these below:
- What’s that device on my network?
- What does my network look like from the internet?
- Am I able to access my [insert service name here] database from here?
Open Source Tool, Nmap, can help answer your networking questions
The occasionally lengthy troubleshooting process associated with answering these questions may be familiar as well, nevermind the unpleasant uncertainty associated with not knowing the answers to some of them. The good news is that one of the most useful open source tools available – Nmap – can help answer these questions and learning its basic usage is pretty straightforward.
Port Scanning for Network Exploration
Nmap – a “network exploration tool and security / port scanner, ” is available from https://nmap.org for practically all OS platforms and is an essential and indispensable tool in the toolkit of many network and security engineers. The term “port scanning” may conjure images of sketchy hacker behavior but it is simply the act of attempting a connection to a TCP or UDP port and observing the result – is the service responding? Have you ever tried to telnet to TCP port 25 to see if the mail server was working? That is a very basic form of port scanning. Port scanning doesn’t become sketchy hacker behavior until you start scanning networks that you aren’t authorized to be scanning, but that’s a different topic entirely.
For the sake of brevity, we will assume that you have downloaded and installed Nmap and will be using the command line version.
We can start off by scanning a host on the internet (scanme.nmap.org) that is provided by the folks who develop Nmap:
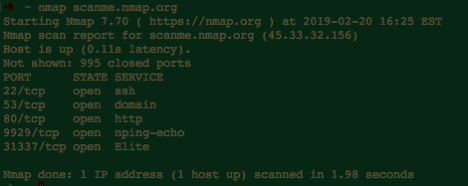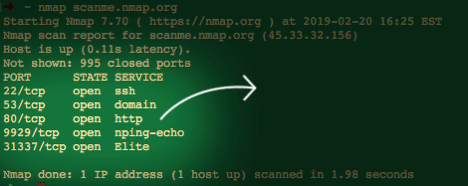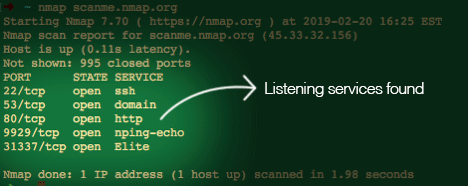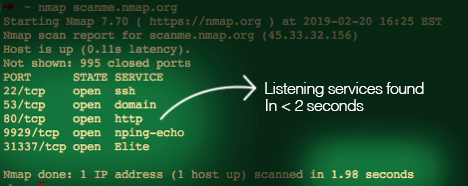
With just a basic scan we determined that the host is up and has 5 listening services in under 2 seconds…pretty cool huh? Let’s try a more detailed scan:
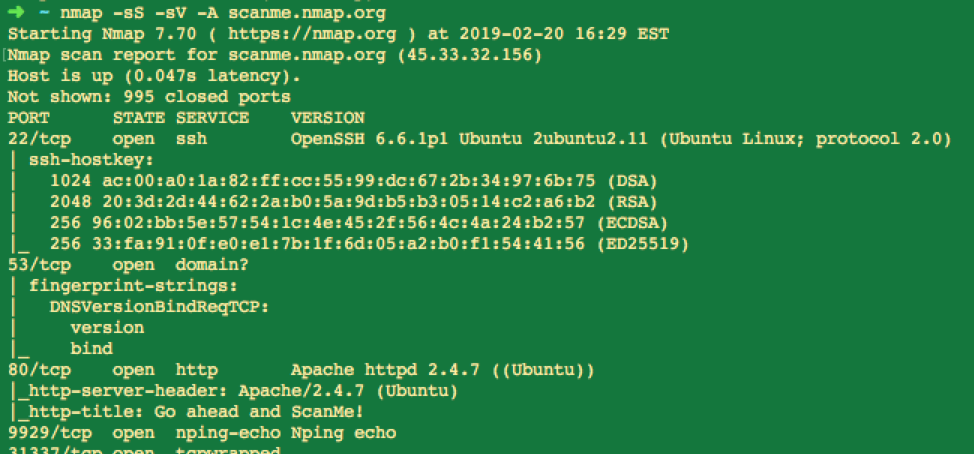
We now have service banners, content from the HTTP server and a pretty good indication of what OS that host is running. I’d say the “network exploration” is going well so far.
Nmap has a ton of features and capabilities which are covered by the great reference at https://nmap.org/book/man.html . Simply running Nmap with no options will also display the usage information as well.
Now that we have done some network exploration let’s get back to some common use cases and see if we can answer some of those questions:
What is that device on my network?
This is a very common scenario and Nmap is really useful for finding out more information. Let’s say I have discovered a device with the IP address 172.17.214.133 on my network but I have no idea what it is. Let’s scan it!
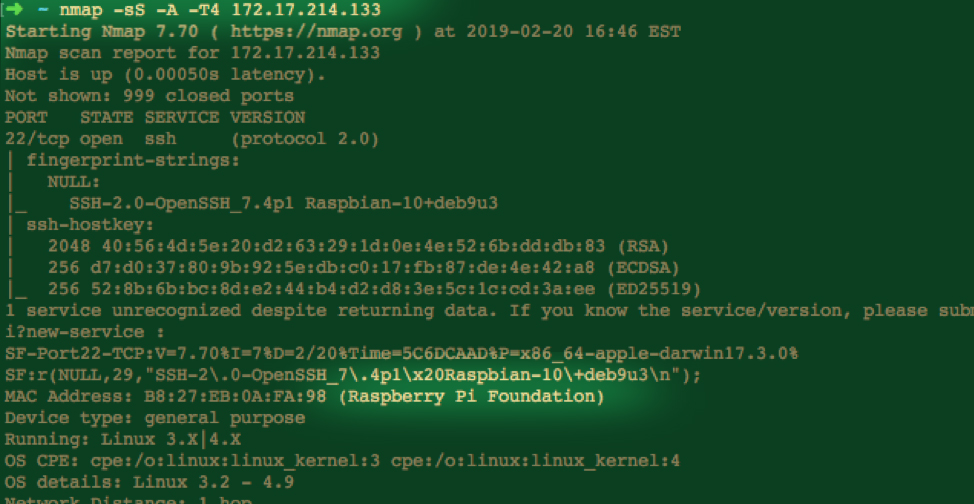
In this scan I have specified “-sS” for a SYN scan “-A” to enable OS detection, version detection and some other features and “-T4” to speed up the scanning. In this case, it looks like we found a Raspberry Pi. Note that since I am on the same subnet we are also able to use the MAC address to identify the device.
What does my network look like from the internet?
Some may think “Oh, I’m not worried about that. We have an Awesome Firewall 5000 that keeps all the hackers out.” Well…are you sure the Awesome Firewall 5000 is blocking everything it’s supposed to? We know that the firewall is part of a multi-layered threat defense architecture (right?) but it would be good to know that it is, in fact, securing the network perimeter as expected. Try scanning your public IP range like so (replacing 192.168.123.0/24 with your IP block):
Nmap -sS 192.168.123.0/24 -oN mynetworkscan.txt
That will perform the same SYN scan on the whole IP range and save the results to “mynetworkscan.txt”
When you test your network perimeter from an external perspective, you to get the most accurate results. Go ahead and give this a try yourself!
