Imagine you’re the coach of a seasoned basketball team. Your squad has played with each another for so long, they can seamlessly execute complex plays, speak the same language, and access resources at any moment- on and off the court. Over time, you have a developed an intricate playbook which serves as the secret sauce to your team’s success. Aided by computer programs analyzing millions of plays and scenarios and coupled with your own discretion, no other team possesses these abundant resources.
The Cisco network is very similar to this well-established team. Now, let’s introduce a skilled player from another organization who speaks an entirely different language, and has no understanding of the existing playbook. This newcomer is talented and performed well on their past team- but you are now faced with the task of integrating the new player without losing efficiency. To be fully effective, each team member needs to speak the same language, access the same resources, understand, interpret and utilize those resources.
When you’re advised to commit to one product line offering, it’s with merit. Cisco’s products and solutions are engineered to work in concert, offering the most comprehensive and robust package in the marketplace. With pressures from the c-suite and boards of directors, it is understood that maximizing the effectiveness of your budget is crucial, and investing in a total package all at once may not be feasible.
Where to Invest with a limited security/IT budget:
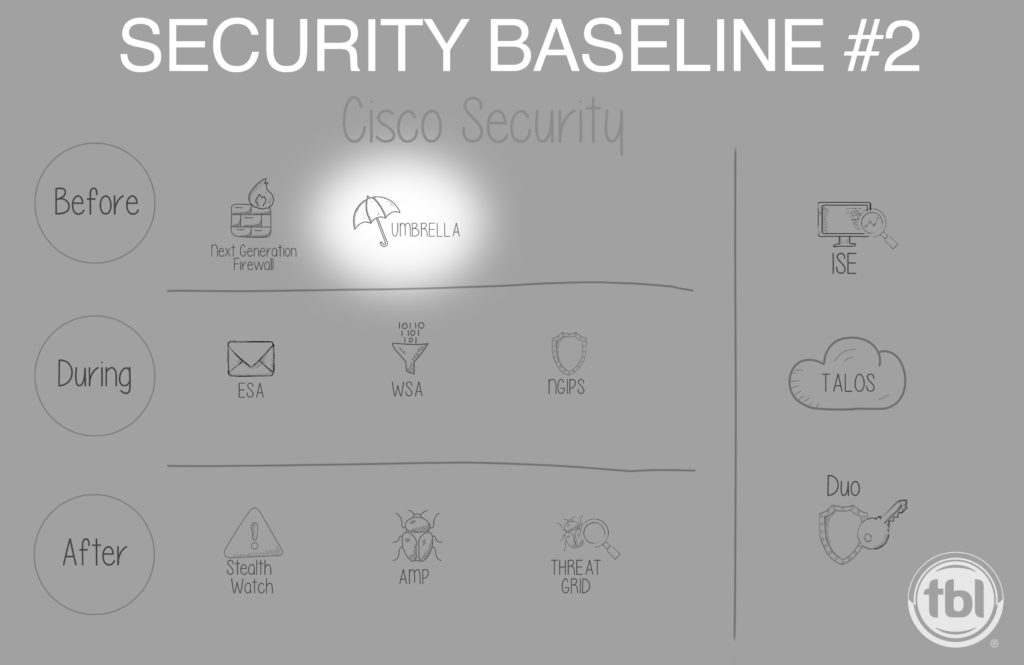
Consider these three security baselines which we’ll cover further for your network: Next generation firewall paired with next-generation IPS, Cisco Umbrella and Duo.
Why have we chosen these three offerings?
- Lower cost
- Simple deployment
- Immediate results
- Strategic placement on the three attack vectors
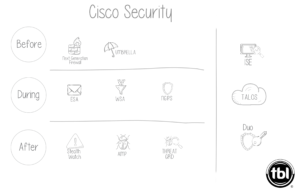
Because no one security tool is impenetrable on its own, strong networks are engineered with layers of visibility into each of the three attack vectors:
- before network entry
- during network entry
- after network entry
When tools are working and reporting at each of these points, more breaches are prevented and the breaches that do occur are resolved more quickly.
Security Baseline #1: Next Generation Firewall (NGFW) with Next Generation Intrusion Prevention System (NGIPS)

Sitting either behind or in front of a firewall on your network, intrusion prevention systems inspects network traffic and looks for known attack signatures. When attacks are detected, IPS alerts users or stops the traffic altogether.
With next generation IPS:
- Extensive coverage of network protocols is included
- Contextual awareness is utilized
- Content awareness such as identifying file types is supported
- Applications and users are identified
- Advanced threats are detected
- Threat intelligence takes action
NGFW and NGIPS access to Cisco’s TALOS – the differentiating and intelligent playbook.
Security Baseline #2: Cisco Umbrella
After processing billions of requests each day from user data, Cisco Umbrella detects malicious domains and blocks them. Built into the foundation of the internet on the cloud, Umbrella identifies attacks such as malware, phishing and ransomware as they are staged on the internet. Working at the DNS and IP layers, it prevents callbacks from exfiltrating data and identities already infected devices. You can try Umbrella for 3 weeks, free!
Security Baseline #3: Duo

Duo is an intelligent multifactor authentication tool. Securing remote access, DNS and cloud apps- it ensures that the right people with the right devices to get the right places. Duo takes multifactor authentication further by profiling users to provide elevate threat protection.
With these three baselines, your network security is off to a strong start. As budget and resources allow, you can continually layer on other necessary components. Need help implementing security baselines? Contact TBL!